Pwn2Own Automotive 2026

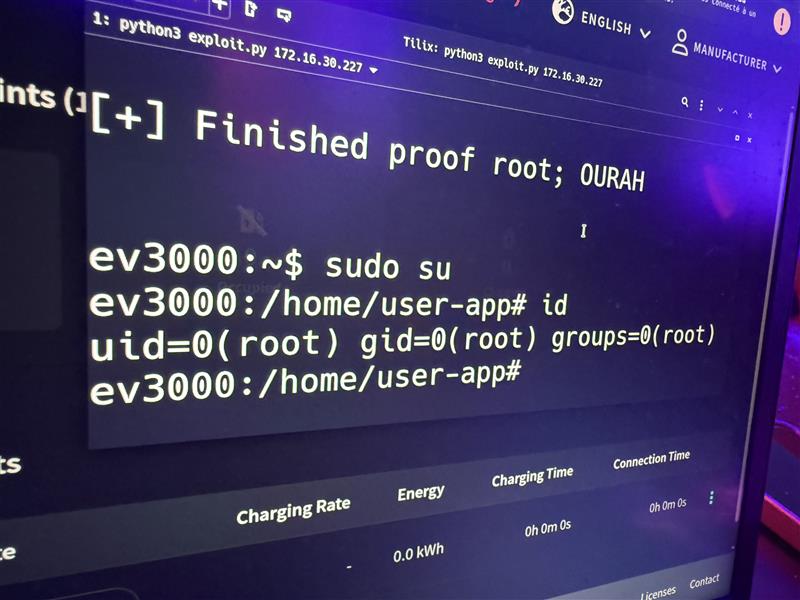
At the latest edition of Pwn2Own Automotive, our member Julien Cohen-Scali demonstrated a successful exploitation of the Phoenix Contact CHARX SEC-3150 in the Level 2 Electric Vehicle Chargers Category as part of his FuzzingLabs job ! We all congratulate him for this achievement !
Here is a description of the device according to the documentation:
The electronics modules of the charging controllers feature the functions and interfaces re-
quired to perform a charging process in a typical AC charging station.
Charging point-specific interfaces and functions
– Interface for vehicle charging connector and infrastructure charging socket with control
of locking mechanism and automatic release of the charging connector in the event of
voltage failure
– Control of the charging contactor
– Connection option for an RFID reader for user release
– Connection option for a sensor for DC residual current detection
– Connection option for an energy measuring device to record the current charging cur-
rent and energy values
– Digital inputs with configurable function assignment
– Digital outputs with configurable function assignment
– Temperature measurement via Pt 1000 sensors or PTC chains
An embedded system with Linux operating system is also integrated in the
CHARX SEC-3xxx charging controllers. This system is the platform for the higher-level ap-
plication software used to control the charging processes and to communicate with external
systems
At Pwn2Own, Julien managed to demonstrate a successful exploitation of the device with root privileges, thus controlling the charging infrastructure and potentially compromising the security of the charging station, and maybe later compromise vehicles connecting to it. The Charx SEC-3150 is a critical part of the charging infrastructure, and its security is of utmost importance. We all congratulate Julien for this achievement !
Pwn2Own IoT 2025

At the latest edition of Pwn2Own IoT, our members Daniel Frederic and Julien Cohen-Scali leveraged an exploit to compromise a QNAP TS-453e NAS device as part of their FuzzingLabs job ! However, due to various small technical issues, the exploit was not successful on stage but was later bought nearly full price by Zero Day Initiative.

Here is a description of the device according to https://nascompares:
Highlights of the QNAP TS-453E NAS:
Intel Celeron 64-bit x86 J6412 4-core/4-thread processor, burst up to 2.6 GHz
- Onboard Intel UHD Graphics, 400Mhz Base Frequency (Burst to 800Mhz)
- 8GB of DDR4 Memory (cannot be upgraded)
- 4x SATA Storage Bays and 2x m.2 NVMe SSD Storage Bays (PCIe Gen 3×2 Bandwith)
- 2x 2.5GbE Network Connectivity
- USB 3.2 Gen 2 (10Gb/s) Connectivity and 2x USB 2.0
- Compact design at 177 × 180 × 235 mm
- 90W External PSU (Power brick in 2 parts)
- 2x HDMI Ports (1.4b Revision and can be used for mirror/extended screen)
at 1080p @60FPS and 4K @30FPS
- Reported Power Consumption at 15.78W in sleep mode and 33.88W when in operation
- EXT4 File System, QTS System Software and Services included
- 2 Surveillance Software Platforms (2/8 Cam licenses), a VM platform, Container App,
Office tools, Multimedia streaming/cataloguing applications, AI Photo recognition
tools and several Backup/Sync tools
- Supports 2x 2/4-Bay Expansion devices or 1x 8/12 Bay Expansion from QNAP
- 3 Year Manufacturers Warranty
At Pwn2Own, we successfully compromised the integrity of the data on the NAS by gaining Remote Code Execution on the device. The exploit is not yet public. We estimated that approximately 15k NAS devices directly exposed to the internet are vulnerable to this issue. Thanks a lot to Zero Day Initiative for buying the exploit nearly full price and hosting this great event ! Congratulations to the team !
Welcome to the new LSE Website
This is the new home for the Laboratoire Système et Sécurité.
We will be posting articles about our projects, research, and CTF writeups here.
Stay tuned for content on:
- Kernel internals
- Hypervisor design
- Reverse engineering challenges
- Exploit development
Don’t forget to check out our CTF platform!